The 'Shellshock' Bash vulnerability and what it means for OS X
Word is spreading on info security websites that there's a vulnerability in a Unix program called Bash. Bash, or Bourne-Again Shell, is standard issue on the Mac, and at this writing, the latest version of OS X — 10.9.5 — has a version that's vulnerable to this new exploit. Should Mac users be concerned about this new security issue? Sure. Should we panic? No, and here's why...
What is Bash?
Bash is a shell — a processor that lets you type commands which then result in actions. It's been around for 25 years, and is the core shell tool used in most Linux and Unix operating systems (including OS X) found in millions of computers all over the world. It can also be used to parse scripts for other programs, like Web servers.
The exploit that's been recently discovered affects all Bash releases through 4.3 — about 25 years worth of Bash versions. So there are a lot of systems potentially affected by this flaw.
What is Shellshock?
The new bug has been nicknamed "Shellshock." The vulnerability lets an outside attacker insert extra code into a Bash command. Researchers are still trying to understand the extent of the exploit, but one of the most prevalent vulnerabilities involves web servers running Common Gateway Interface (CGI) scripts, a standard method for creating dynamic content on the web. An attacker uses "environment variables" containing Bash functions in them. You can read more about it here. Warning: It's pretty dense technical language.
Arbitrary code execution is a very serious problem. The worst case scenario is that an outside attacker can take over the targeted computer, access files and get it to run software it wouldn't otherwise.
Shellshock is being compared to Heartbleed, a bug involving a popular security library called OpenSSL. There's no direct correlation here, but like OpenSSL, Bash is broadly used by computers all over the Internet, so there's concern that many will go unpatched and hackers will use the exploit towards their own ends.
Back to the Mac
OS X Mavericks 10.9.5 includes Bash 3.2, a version of Bash that is vulnerable to the exploit. As this was posted, Apple had not yet released a security patch to update the version of Bash included with Mavericks.
Master your iPhone in minutes
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
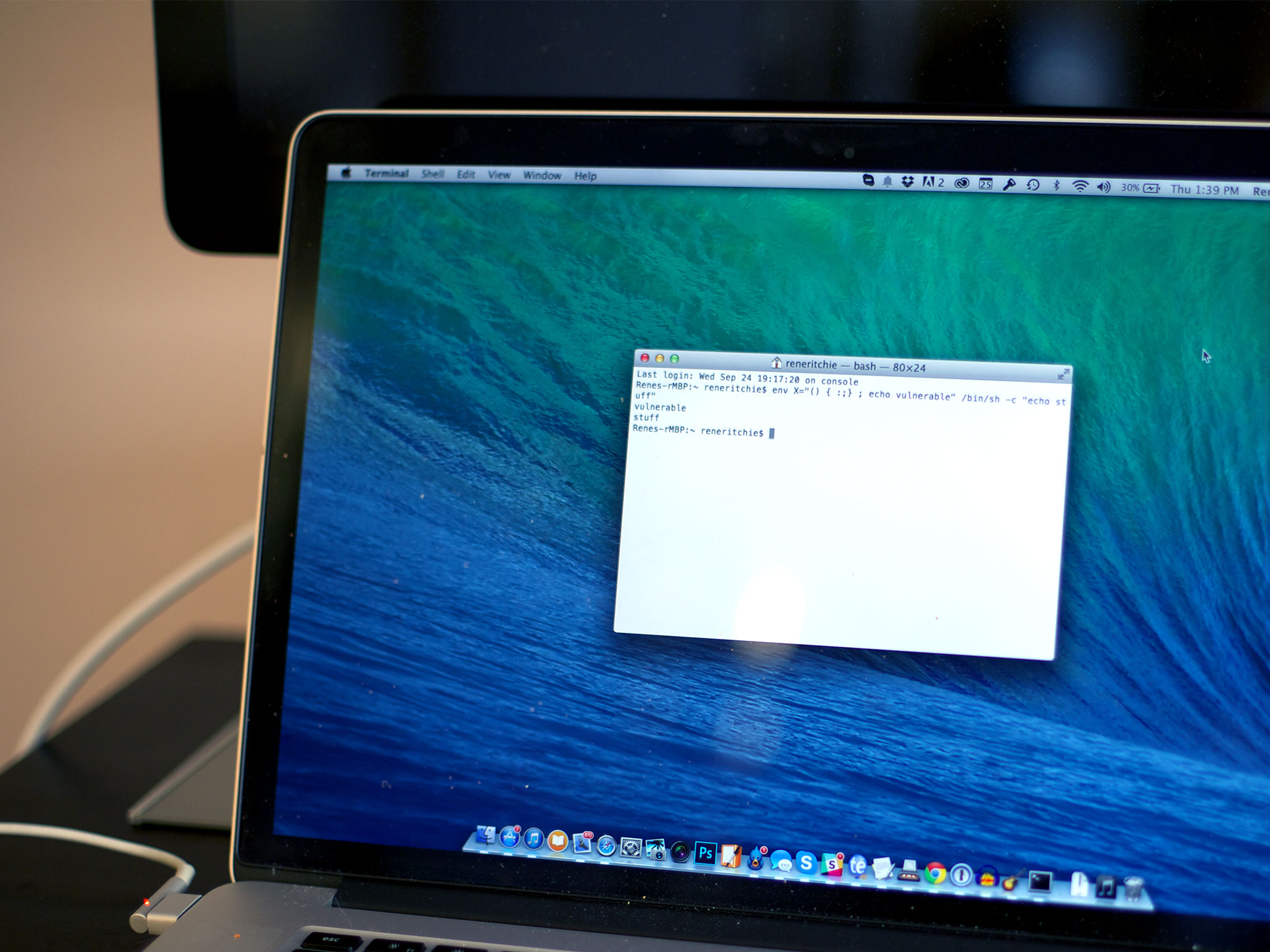
You can test your Mac yourself using a simple command in the Terminal application.
Testing for the Bash vulnerability
- Double-click on the Utilities folder.
- Double-click on Terminal.
- Type (or copy and paste) the following command: env X="() { :;} ; echo vulnerable" /bin/sh -c "echo stuff"
If your Mac says "vulnerable," then the version of Bash installed on it is indeed vulnerable to the problem.
But that doesn't mean that your Mac can be exploited by hackers. You'd have to be running software that is accessible to the outside world and invokes Bash when it is run. So far I haven't seen any exploits that the average Mac user would need to worry about.
What now?
System administrators and IT personnel responsible for managing Internet-facing servers need to be on high alert at this hour, patching vulnerable systems with an updated release of Bash or even using a shell program besides Bash until a better solution is available.
StackExchange has an explanation on how to patch the Macintosh version of Bash, but this isn't something I'd recommend for the lay user. For one thing, it depends on having Apple's Xcode programming environment installed on your Mac. For another, it depends on being comfortable using the Mac's command line interface via the Terminal program.
For those reasons, I'd recommend holding off until an officially-brewed fix is ready from Apple. Given the high public profile of this particular problem, I hope that won't be too long.
Are you concerned about the Bash vulnerability? Are you waiting for Apple to update security on Mavericks and other operating systems? Let me know in the comments.