What's really happening with iOS 8 MAC address randomization?

Normally when you're walking around with a WiFi-enabled device, if it's not connected to a network, it's broadcasting probes in order to try and find known networks. These probes would be sent using your phone's WiFi MAC address, which is a unique and normally persistent value. This means that anybody monitoring these probes, say in a department store for example, can persistently track you through a store and across multiple visits. This information isn't tied to your personal identity, but a lot of information about your shopping habits could be gleaned from this data by analytics companies, and some users aren't thrilled about not having a say in this. And remember, this isn't just an iPhone thing, this is a WiFi thing. This is what devices do. But Apple decided they could do better.
How it's supposed to work
Starting in iOS 8, devices are supposed to randomize their MAC address when broadcasting these WiFi probes. The OS is responsible for creating random, locally administered MAC addresses. The hope is that so long as you aren't connecting to wireless access points, your device can't be used to track you anymore. Because these are WiFi probes, their range is limited. Somebody wanting to track the presence and movement of your device would need to be in relatively close proximity. One place we've seen devices like this used is in department stores to monitor the shopping habits of customers. With a new random MAC address periodically being generated for your device, there would no longer be a persistent token for passive monitors to track your device with.
How it seems to work
Unfortunately, it looks like Apple's changes to the behavior of these probes isn't quite what we had hoped for. A couple of weeks ago a representative from an indoor navigation and location analytics company, GISi Indoors reached out to us saying that they had been testing this change of functionality in every iOS 8 beta, and had yet to see it work. We fired up Wireshark to take a look for ourselves.
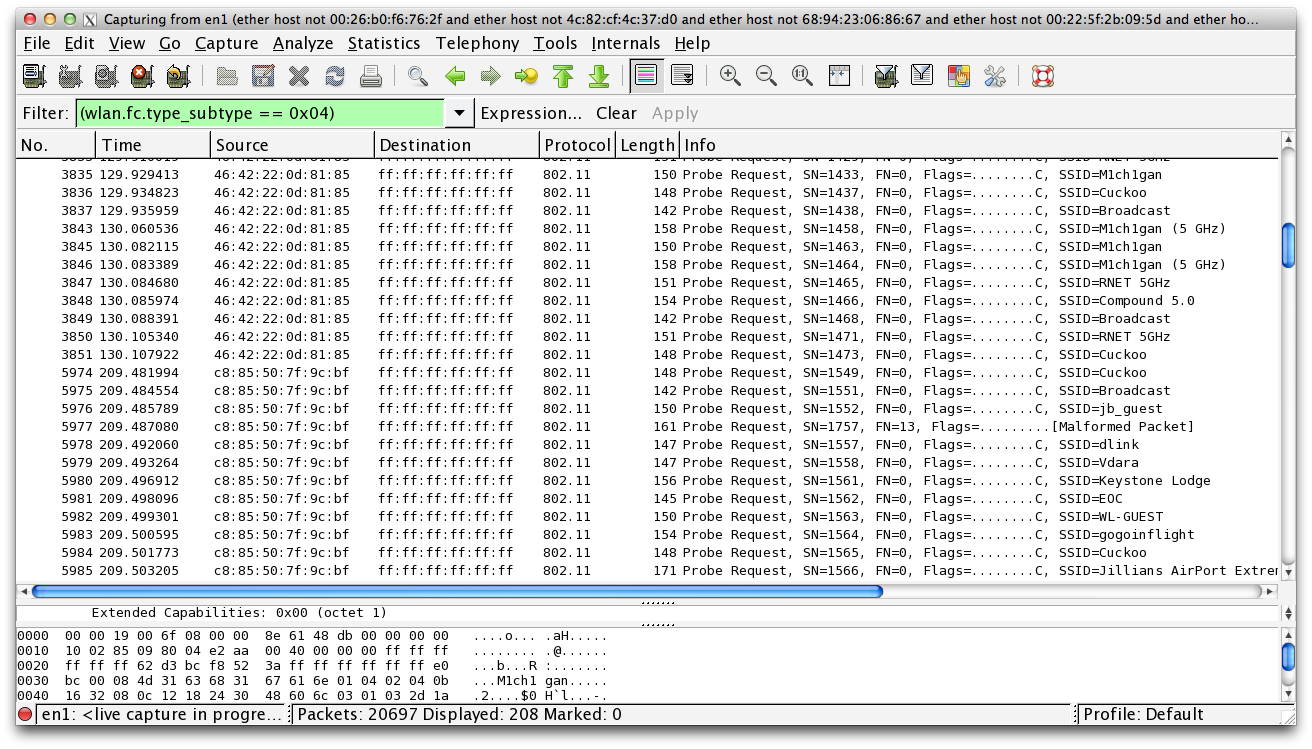
Sure enough, we saw our device gleefully firing out WiFi probes using its real MAC address, and we weren't alone. Security researcher, Hubert Seiwert responsible for the tool iSniff saw the same behavior. Initially it looked as if MAC randomization didn't work at all, which was confusing because Apple has made a point to publicize this feature.
After a lot of digging and a lot of late nights monitoring Wireshark captures, it looks like Apple has shipped this feature as advertised, but not quite as expected. In the WWDC session on user privacy, the slide said "The MAC address used for Wi-Fi scans may not always be the device's real (universal) address". They didn't say it would never be a device's real MAC, only that it may not always be.
Last week, analytics company AirTight Wireless published extremely detailed reports of their testing of iOS 8 MAC randomization and found similar results. If you haven't read it yet, I strongly encourage you to go take a look. Their testing seems to be very extensive, though their findings didn't completely align with ours.
In our testing we found that in order for the MAC randomization functionality to work, supported iOS 8 devices must meet two criteria. First, the device must not be connected to WiFi, which makes sense. Second, the device must be asleep. AirTight concluded that Location Services and cellular service also have to be disabled, but after taking a close look, I don't think this is the case. I think what's happening is the "device must be asleep" requirement makes it difficult to tell what's going on when monitoring this traffic.
Master your iPhone in minutes
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
On an iPhone 6 running iOS 8.0.2, I was able to observe WiFi probes being sent with a randomized MAC address with Location Services and cellular service enabled. The problem is if you have a cellular connection, your phone doesn't tend to stay asleep for very long. Even if your screen is asleep your phone may not be as it, for example, receives a new email via push. Even if you have notifications turned off, your phone wakes up when that email comes in, despite the screen staying off.
Unfortunately, the requirement of the phone being asleep makes this feature nearly useless, albeit within the description of what Apple advertised at WWDC. In order to get random MACs to be used I had to turn off notifications for multiple apps, turn off push email, and stay up late at night when there was a greater chance of my phone getting to sleep, uninterrupted, for more than a minute or two. Even under these circumstances, I would only encounter one or two rounds of probe beacons (which seem go to out every couple of minutes) with a random MAC before seeing my phone blast a bunch of probes with my real MAC. My best guess is this would happen when some process of push had woken the device up. With cellular data turned on, only about 50% of the probes I saw go out had a randomly assigned MAC.
Rendering this feature even more useless, when the probe requests went out with a random MAC, the probes contained SSIDs of 5 networks that the phone had previously connected to. This means even when my MAC is random, the SSIDs it's broadcasting can act as a fingerprint for my phone. My MAC can be different every time probes go out, but if it broadcasts the same set of 5 network names every few minutes, it may still be possible for monitors to track my device.
Should we be worried?
Ultimately this feature wasn't something Apple had to do, it's something they decided to do to help user privacy. While it was a great idea in theory, the execution seems to have fallen short of anything really useful. Users aren't any worse off than they were with iOS 7, and this information still doesn't tie directly to a person, but it does give companies (and individuals) the ability to track an anonymous person without their consent. This is primarily only useful to stores, marketers, and analytics companies for analyzing trends and habits of consumers, but ideally it's something users have some control over. This data effectively amounts to information about us, and we should have the final say in who can use that data. Hopefully Apple can make adjustments to when MAC randomization occurs to increase the scenarios in which an iPhone's real MAC address is used. While not practical for many, people looking to avoid being tracked in the meantime can disable WiFi or enable airplane mode.

