iOS Personal Hotspot passwords vulnerable to brute force attacks
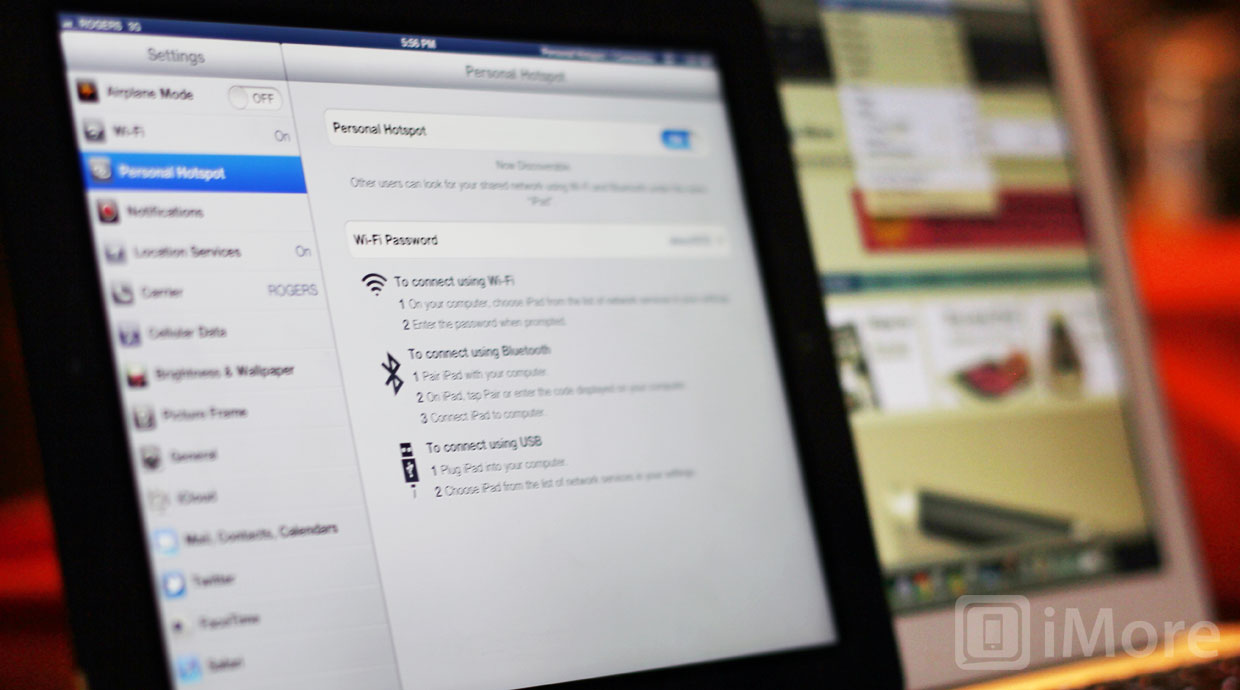
Researchers at the University of Erlangen-Nuremberg have discovered weaknesses in the Personal Hotspot feature in iOS. The weak, and somewhat predictable password generation -- used in all current versions of iOS up through iOS 6 -- means people are susceptible to brute force attacks when using the personal hotspot feature on their iPhone or cellular iPad.
A brute force attack is one that systematically tries all possible combinations of a password until the correct one is found. The more complex a password, the more computing power and/or time it takes to try the combinations. Under Settings on iOS, inside Personal Hotspot, you will normally find Wi-Fi Password to be pre-populated with a memorable password followed by four digits. Andreas Kurtz, Daniel Metz and Felix C. Freiling found that iOS chooses from only 1,842 words in a wordlist, each 4 to 6 characters in length, when generating these default passwords. iOS generates these passwords with one of the words from the list, followed by a four-digit number. This combination only leaves the possibility of about 18.5 million different passwords, a relatively low number when it comes to password cracking, making it an easy target for a brute force attack. It was also discovered that words from the list aren't chosen randomly, and some words are chosen much more frequently than others. This knowledge can potentially speed up the process of cracking the password by trying the most commonly chosen words first. The researchers state that all of these factors make it possible to compromise a hotspot connection in less than 50 seconds.
The Personal Hotspot feature employs WPA2-PSK encryption, which is generally regarded as secure for WiFi. However, the short list of known passwords being used in iOS means that these default passwords are extremely susceptible to brute force attacks. When a device connects to a hotspot, a handshake takes place in which the client and the hotspot negotiate their connection. This is also the time where the client authenticates with the hotspot using the pre-shared key. By capturing this handshake, an attacker is then able to run a brute force attack using the known word list to generate and attempt all 18.5 million possible passwords, until it finds a match. Once a match is found, an attacker could then connect to your personal hotspot to use your connection, or potentially leverage further attacks against other connected devices. The report also mentions that other mobile platforms showed signs that they were affected by similar problems, including Windows Phone 8 and some vendor-modified versions of Android.
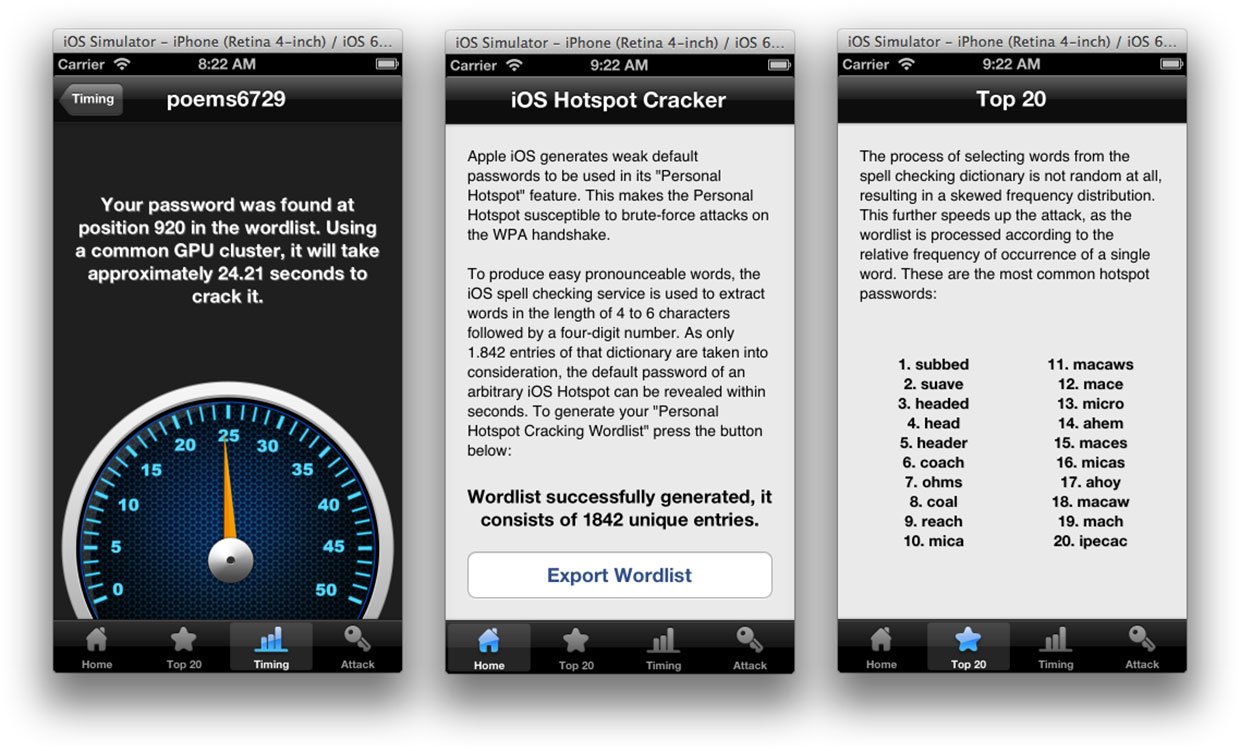
The researchers also released the source code for Hotspot Cracker, an iOS app that demonstrates their findings. The app allows you to generate and export the wordlist from iOS, view the 20 most common words used for personal hotspot passwords, enter your hotspot password to find out approximately how long it would take to crack, and gives instructions on how to crack a password once you have captured the handshake. When calculating how long it would take to crack your password, the app presumes a GPU cluster of four AMD Radeon HD 7970s, which can run about 390,000 guesses per second. With these calculations, the app determined my iPhone's personal hotspot password would take just under 25 seconds to crack.
The reason iOS and other mobile platforms generate passwords automatically is to avoid having users set up hotspots without any encryption. These passwords are certainly better than having no encryption at all, but this research shows that these passwords should not be considered secure.
iOS shows you how many devices are connected to your hotspot, making it easy to recognize if there are ever more devices connected than you expect.
Until Apple changes to more secure defaults, the easiest thing for iOS 6 (and earlier) users to do is simply set their own unique password for Personal Hotspot.
Master your iPhone in minutes
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!

