Find my Mac passcode lock brute-force attack: What you need to know!
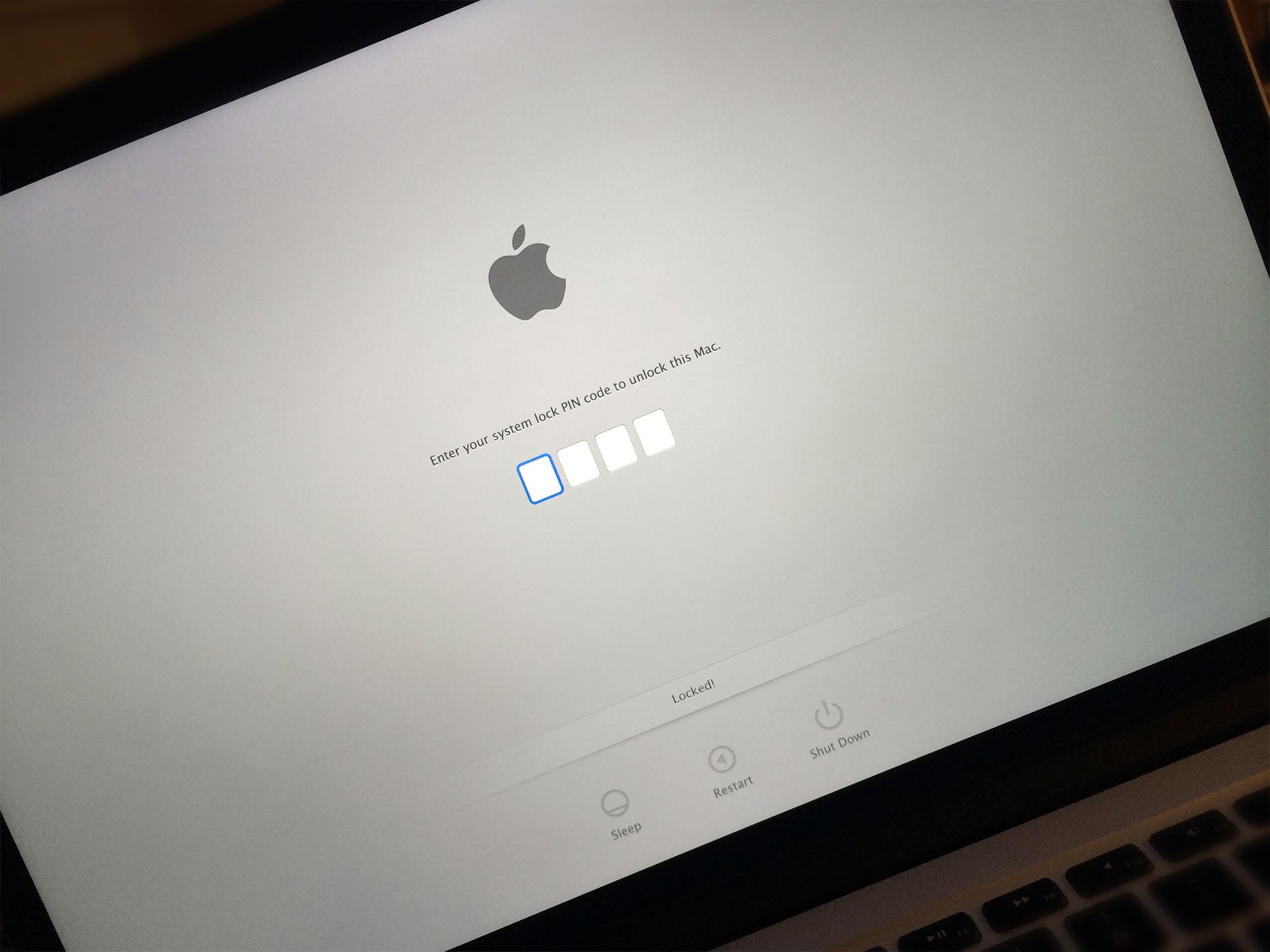
When Apple launched Find my Mac as an extension to their Find my iPhone system back in October of 2011 they included the ability to lock a Mac down so that it couldn't be accessed or rebooted into alternate modes. The lock, however, was implemented using a simple 4-digit passcode (PIN). That meant, with only 10,000 possible combinations, the passcode was susceptible to brute force attack. That's nothing new. It's been known since the start. What's new is that automated tools have now been developed to make the attack both easier and faster, and they're being reported on without a lot of context. So, is it something you should worry about?
A 4-digit passcode is the same basic type of protection offered on iPhone and iPad, but iOS devices are far more difficult to brute force and so far — outside of jailbreak — haven't been susceptible to automated attacks. Also, iOS offers the option for a much more secure, much stronger alphanumeric password to be set on the device.
With automatic login turned off on your Mac, entering the Find my Mac passcode will simply reboot the machine into the OS X login. That password should be more secure than a passcode anyway, and at the very least is an additional layer of protection.
An attacker with the physical access to your machine required to brute force a Find my Mac passcode also has the access required to crack the casing open, rip out the disks, and mount them on another, unlocked machine to access your data that way. That is, of course, unless you have FileVault disk encryption enabled. (FileVault, by the way, removes automatic login as an option.)
If you have both a strong OS X login password and FileVault encryption set up on your Mac, then you only ever have to use Find my Mac's lock feature if you've left your computer logged in and unattended and have a sudden reason to fear for its security. In that case, it works fine and any attacker intent and sophisticated enough to brute force the passcode would be greeted by the awesome OS X head-shake animation and a bunch of gobbledygook on the drive.
If you've inexplicably decided not to disable automatic login and use FileVault, and you have to use the Find my Mac lock feature to keep someone from getting into your computer, then, yes, a sophisticated attacker could either brute force your passcode or simply rip out the disk.
I'm not sure if Find my Mac's lock forces an OS X login even if automatic login is enabled — all my Macs have FileVault on so I can't test it. I'd be tempted to say even the option for weak, remote passcode protection on OS X is better than the lack of any similar option on other systems but, drive yank.
Master your iPhone in minutes
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
So, there are three take-aways here:
- You should, If you're worried about security, disable automatic login. You should also, if you have data you absolutely want to keep safe no matter what, turn on FileVault. That will stop anyone this side of a billion-dollar supercomputer from getting to your data even if they have physical access to your drive. Sure, that's less convenient but security is sometimes more important than convenience.
- Apple should provide the option for a stronger, alpha-numeric password for Find my Mac locks. Sure, that would increase the chances of a person using the lock and forgetting the password, especially in a panic. However, since passwords have to be confirmed, anyone who switches to the advanced option should be able to retain the password thy enter long enough to mark it down somewhere safe.
- People who publish articles on Apple security, especially in the post-SSL/TSL bug climate, should do their best to provide proper context and threat assessment along with it. Sure, informing people is vital. Scaring them disproportionately is not.
Are you using the OS X login and FileVault currently and, either way, does Find my Mac being restricted to a 4-digit passcode concern you?
Nick Arnott and Anthony Casella contributed to this article.

Rene Ritchie is one of the most respected Apple analysts in the business, reaching a combined audience of over 40 million readers a month. His YouTube channel, Vector, has over 90 thousand subscribers and 14 million views and his podcasts, including Debug, have been downloaded over 20 million times. He also regularly co-hosts MacBreak Weekly for the TWiT network and co-hosted CES Live! and Talk Mobile. Based in Montreal, Rene is a former director of product marketing, web developer, and graphic designer. He's authored several books and appeared on numerous television and radio segments to discuss Apple and the technology industry. When not working, he likes to cook, grapple, and spend time with his friends and family.
