Apple's lofty goal for macOS Catalina is to make the system as secure as iOS while maintaining all the traditional flexibility of the Mac. And… that's easier said than done. With iOS, Apple got to start fresh and lock everything down since day one. The Mac, by starkest of contrasts, has been relatively open for decades.
For many years, that was fine. Thanks to the market share and attack surface of Windows, it made far more economic sense for bad actors to go after Microsoft users and leave Apple users alone.
But, now we have the web, we have phishing and spear-phishing, ransomware and spyware, we even have ad trackers and social networks and the ability and eagerness of bad actors and unscrupulous companies to target any and every platform and person, including those of us on the Mac.
So, Apple has been carefully hardening macOS against exactly those kinds of attacks. Carefully, because people who are used to the Mac being open are concerned — legitimately sometimes, completely paranoid others — that Apple is going to impose the same type of control it has over iOS.
Over the years we've gotten Gatekeeper to prevent unauthorized apps from running, and System Integrity Protection to stop anything from modifying the operating system, and social tracking and fingerprinting… well, that's been shut down.
With MacOS Catalina, Apple is perpetrating some of their biggest security and privacy balancing acts ever. All in the name of continuing to let us do what we want with our Macs, but locking out everyone else.
Gatekeeper
Apple thinks about security on the Mac the way pretty much anyone in the industry would tell you they should think about it — through defense in depth.
That means multiple layers of security to prevent or delay attacks from happening, reduce the attack surface and create choke points that are easier to defend, like only running trusted apps, minimizing and containing anything that does get through, like with sandboxing, and dealing with anything that somehow makes it onto the system, like revoking a trust certificate.
Gatekeeper is the starting point. Currently, when you download an app, whether it's off the Store or the Web or even from AirDrop, that app is quarantined. If and when you try to open a quarantined app, Gatekeeper checks it for known malware, validates the developer signature to make sure it hasn't been tampered with, makes sure it's allowed to run, for example matches your settings for App Store apps and/or known developer apps, and then double checks with you that you really want to run the app for the first time, that it's not trying to pull a fast one and autorun itself.
Something similar happens with files you download directly from the web or through a sandboxed app or get AirDropped as well. Basically, most things hitting your device for the first time.
But, up until now, Gatekeeper had some limits. It only checked quarantined apps and only when you tried to run them using the graphical interface, in other words with LaunchServices, the very first time you tried to run them.
For example, double-clicking on an app to run it or a file to open it.
With Catalina, Gatekeeper will also check apps launched via the terminal as well. They'll get the same malware scan, signature check, and local security policy check. The only difference is, even on first run, you only need to explicitly approve software launched in bundles, like a standard Mac app bundle, not for standalone executables or libraries.
What's more, Gatekeeper will now also check non-quarantined apps and files for malware. In other words, the second time, third time, four hundredth time you run it, every time you run it, Gatekeeper will check for malicious content and if it ever finds any, block it and alert you.
Of course, because the Mac is the Mac, you can still override all of this if you really want to and run anything you want, any time you want, and the Mac you want.
Read-Only System Volume
What's the point of security if anything that tries hard enough can just write all over the root files anyway?
That's not really something anyone says, but it is something macOS Catalina is addressing with dedicated, read-only hardware partition for the root file system to keep it separate and secure from the rest of your data and reduce the chances anything can corrupt or infect it.
To make it work, the Apple File System, APFS, is introducing the concept of a volume group. That's a set of one system volume and one data volume, paired, and treated as a single volume.
They show up as a single volume, they share encryption state, which means the same password unlocks them both, and are otherwise almost indistinguishable to a casual observer.
They even maintain a single, unified directory hierarchy through another new concept called firmlinks, which Apple calls bi-directional wormholes in path traversal. Ha.
Firmlinks are created at install time and are transparent to users. They can only be for directories and have a one-to-one relationship, like Users to Users and Local to Local. No-one-to-many — totally monogamous — and can only be used in volume groups between the paired volumes. This isn't files gone wild, people.
Now, just like System Integrity Protection and T2 could annoy people trying to run new versions of the OS on no-longer supported hardware or trying to install alternate operating systems, this can do things like preventing custom icons for existing apps.
So, you can disable read-only if you absolutely want to by disabling System Integrity Protection, but it will revert to read-only the next time you reboot.
APFS has also added snapshotting, so, if something goes wrong after an update, like some of your apps end up being incompatible, you'll be able to restore from the snapshot and basically Quantum Realm your system back to the point before the upgrade snapped.
Snapshots only last for a day, and only if you have enough space on your drive, so if you ever need to use the feature, use it fast.
System Extensions & DriverKit
Apple has also added two new technologies to Catalina, to better protect the operating system but also allow a range of useful features. They're System Extensions and DriverKit
System Extensions replace the old Kernel Extensions, or KEXTS, but run in user space, safely outside the kernel. Network Extensions support content filters, DNS proxies, and VPN clients. Endpoint Security Extensions replace kauth event monitoring and can be used for endpoint detection and response, anti-virus, and data loss prevention tools. Driver Extensions replace IOKit device drivers and support USB, Serial, Network Interface Controller, and Human Interface devices.
That last one is built using DriverKit, which is a new set of frameworks, updated and modernized from IOKit, so that drivers can be built more safely and securely outside the kernel. Which means, if they have a vulnerability, it doesn't expose the kernel and its privileges to exploitation. And if it crashes, it doesn't panic the kernel and take down the whole system like some Guru Mediation Error gone wrong.
Everything, all of it, stays far more safely in userland where it now belongs.
Data Protection
Just like Apple has previously added the requirement for apps to ask permission before they can use the mic and the camera, Apple is now requiring apps to ask permission before they can access your data in the file system as well.
It doesn't matter if that data on the desktop, or in documents, downloads, iCloud Drive, other cloud storage systems like Dropbox or Google Drive directories, external storage like USB drives or SD cards, or network-attached storage volumes.
The apps, they've got to ask.
To avoid a Windows Vista-like death-by-a-thousand-dialogs situation, Catalina won't intervene when a new file is created, if a file was created by the same app trying to access it, if it's a related file like the subtitle file for a movie file, or if you do something deliberate and intentional, like double-clicking a file in Finder, dragging and dropping a file, or use the standard open or save file function. The system will only intervene if the app tries to open something without any overt action on your part.
Further, Open and Save panels are now hosted out-of-process, and the OK button on consent dialogs can't be handled programmatically. An actual human has to hit that button.
No tomfoolery or skullduggery allowed.
Also, yes, apps can still dump their own files into the trash, but if they want to go rooting around in your trash for other files, which may contain sensitive data, they now need your permission to do that as well.
For disk management or backup software that needs to work with all files on the system, there's a Full Disk Access option in the Security & Privacy preferences pane where you can grant them the permission they need to operate. And, to make that easier, any app that's already tried and been denied full system access, will show up, unchecked, in the list so you don't have to go spelunking through the file hierarchy to find it. Now that, SuperDuper. Sorry.
For automation, in addition to the synthetic input events, like virtual key presses or mouse clicks, and Apple events, including AppleScript, used by one app to control another.
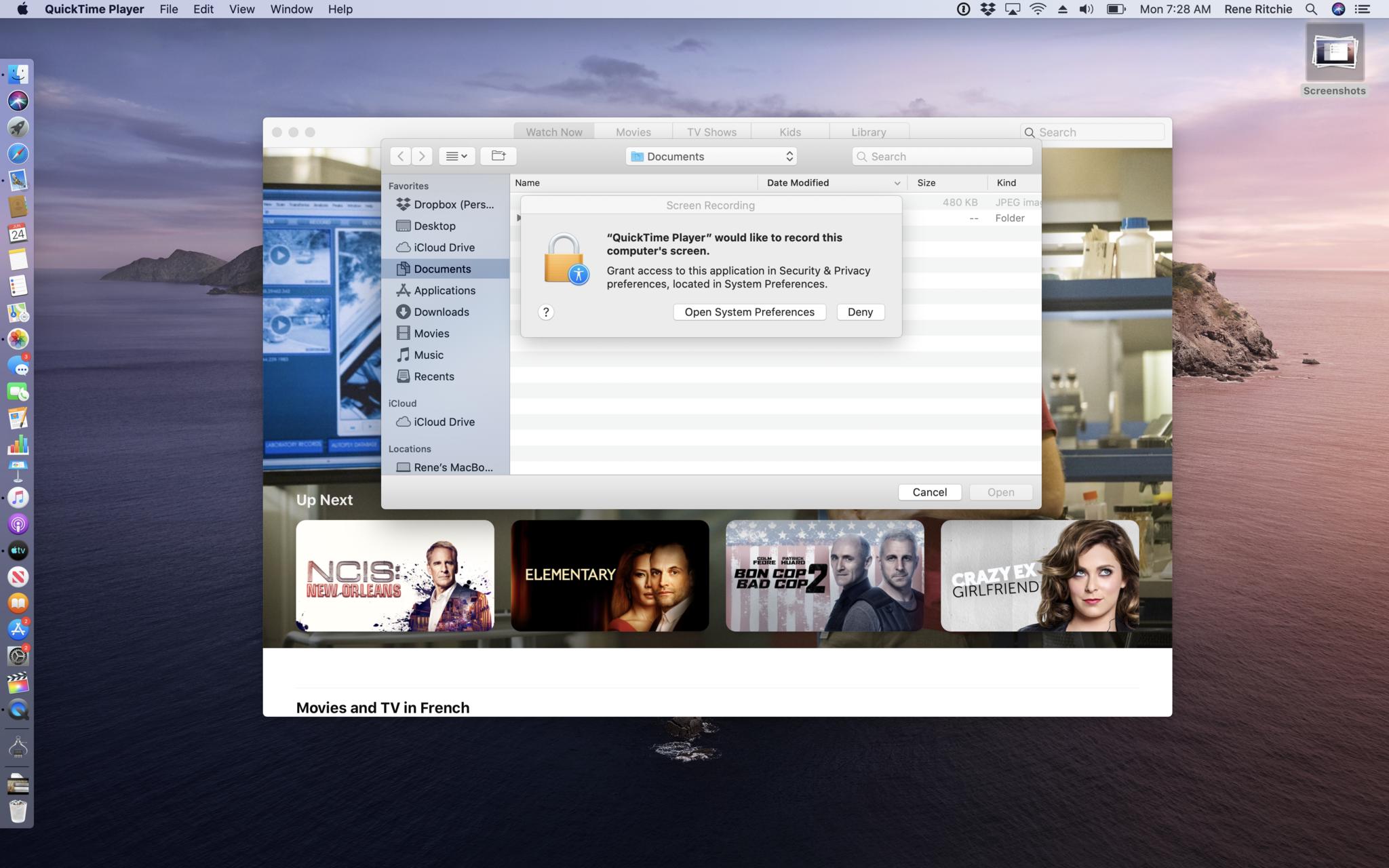
In an effort to make spyware even harder to sneak into apps, Catalina adds new protections for screen recording and keyboard monitoring as well. If an app wants to record the entire screen, or any screen other than its own, the menubar, or the desktop without any desktop icons, you have to go to the Security & Privacy pane in preferences and give them explicit permission to do so. And, honestly, I wish Apple would exclude the desktop as well. My Fraggle Rock wallpaper — or any family or friends on my desktop — are my business.
Similarly, apps can still query most metadata about other windows, but can no longer get other window names, which could include sensitive information like accounts or URLs, and sharing states without express screen recording permissions.
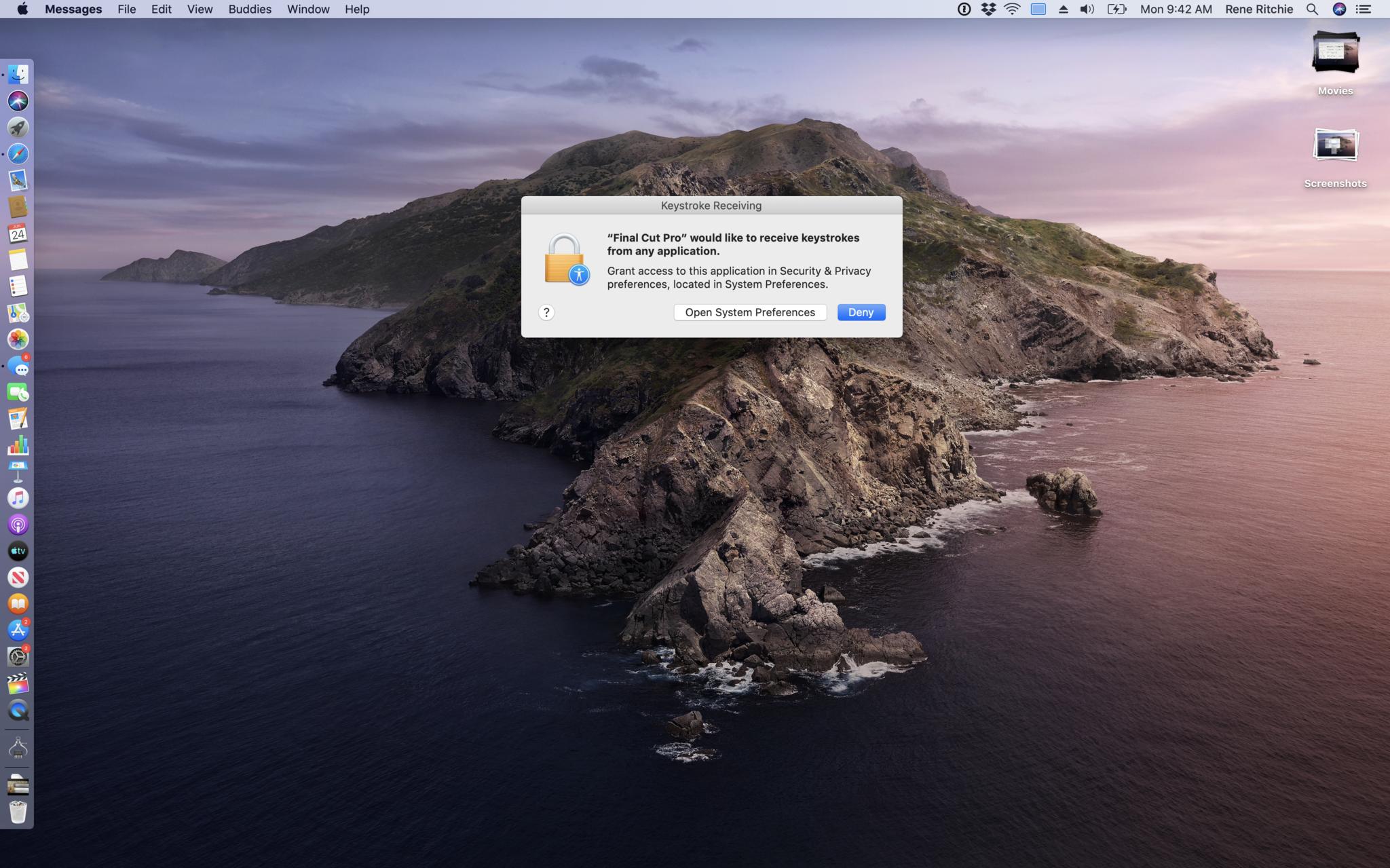
Likewise, apps can monitor keyboard events for themselves without any extra permissions. If they want to intercept all keyboard events, for example, for a specific hotkey combination, you again have to go to the Security & Privacy pane in preferences and give them explicit permission.
Authorize with Apple Watch
Previously, you could use your Apple Watch to unlock your Mac or approve Apple Pay transactions. The latter was mostly for cases where your Mac didn't have Touch ID to make approval faster and more convenient.
But, if you didn't have Touch ID, which is still now only found on the MacBook Pro and new MacBook Air, not the MacBook or any of the desktop Macs via Magic Keyboard, Apple Watch couldn't help you. All it could do was look on as you manually authenticated…. Like an animal.
Or worse, left authentication off… like some kind of crazy rock headed creature from Salsa Secundus.
Now, with MacOS Catalina, you can use your Apple Watch to authenticate pretty much everything Touch ID can, including viewing saved passwords in Safari, unlocking secure Notes, and approving new app installs from the App Store.
Just click the Side Button and, if your Apple Watch hasn't left your wrist and lost your heartbeat and gone into lockdown, it'll authenticate you right up. Quick and easy.
I still want a Magic Keyboard with Touch ID and a Cinema Display with Face ID, but I'm wicked happy with this in the meantime.
Apple ID
iOS has had your Apple ID front and center for a while now in Settings. It makes it super easy, barely an inconvenience to check and manage your account. macOS Catalina adds the same ease and convenience to System Preferences. It puts your Apple ID right up top, alerts you to anything you need to know, lets you review your information, security settings, payment info, and iCloud account pretty much immediately.
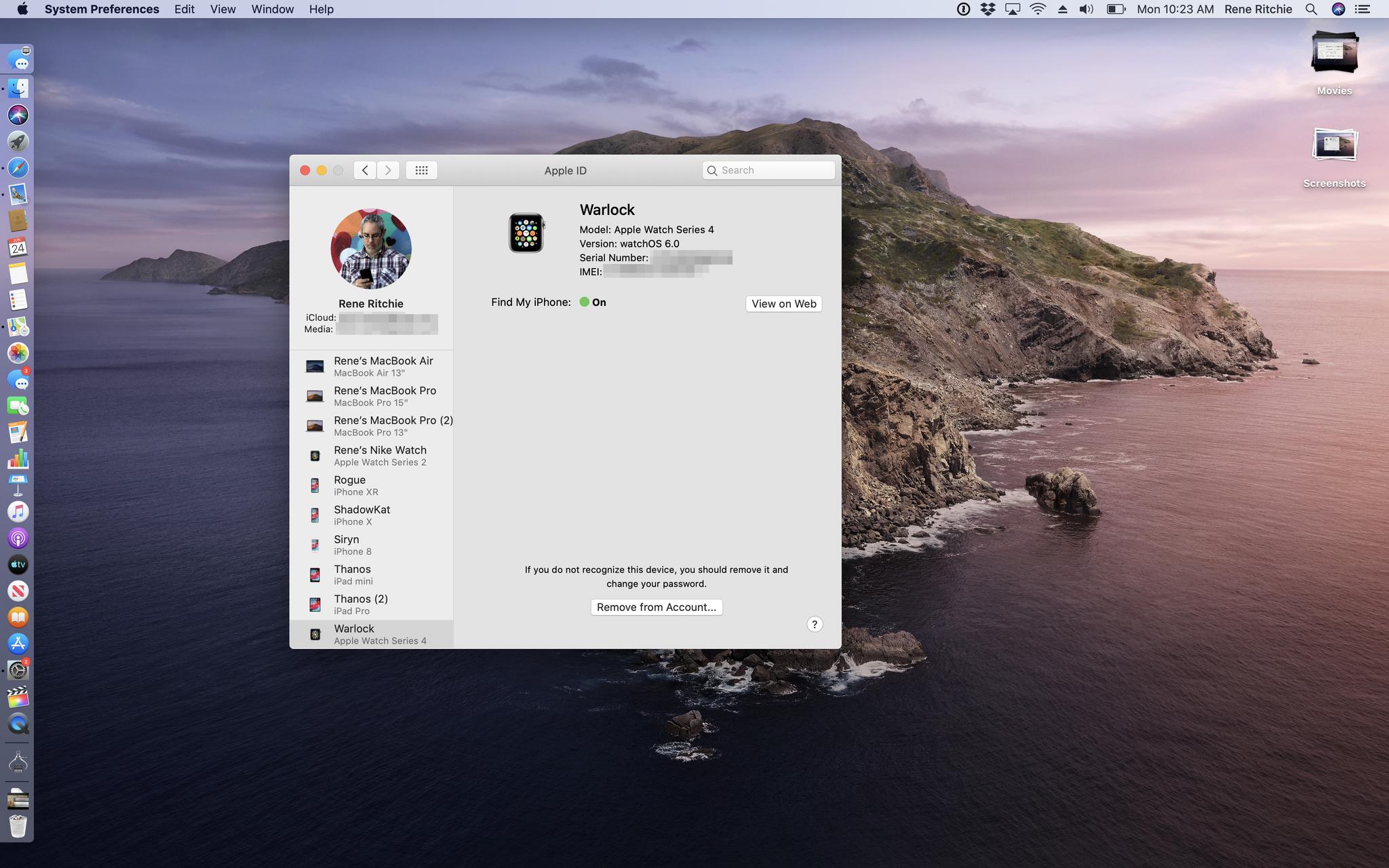
You can also see all your iTunes Store purchases and subscriptions, including Music, Books, News, and app-related subs as well, and manage Family Sharing if you have it. Plus, you get your full device list, so you can manage other Macs, iPhones, iPads, whatever is on your accounts, including Find My status, Apple Pay authorizations, and AppleCare information.
This is huge for me. I have the non-normal problem of having adding too many review units to my account over too many years. Who knew there was a hard limit on Apple Pay devices? 10, if you didn't. And trying to manage that through iCloud.com had never been easy.
With Catalina, a few clicks and I was done. It's Apple ID bliss.
Sign in with Apple
I also want to mention Sign in with Apple. I've already been covering it as part of iSO 13 but it's going to be available on all of Apple's platforms, including the Mac.
The gist is this — Download an app, like a new image editor, and if it offers sign in with Google and Facebook, it has to offer sign in with Apple as well.
If the app doesn't care about your data and just wants you in as fast as possible, it just let you click and start working. If it wants some data first, like your name and email, Sign in with Apple will give it your verified Apple ID name and, if you're ok with it, your verified Apple ID email address as well.
If you're not ok with it, Sign in with Apple will create a burner address for you, random, anonymized, that you can reply to if and when needed, but also revoke any time, just for that app. And Apple never sees or retains any of these emails.
And because they're all unique, companies like Google and Facebook which try to connect all our dots see only dead ends.
If you already have an account, like from another app by the same company, and it's already in your Keychain, Sign in with Apple is smart enough to just give you that to log in with instead, that way you're not creating duplicate accounts or losing access to anything valuable in any existing accounts.
For us it means less passwords to remember and, because it uses Apple's two-factor and Face ID or Touch ID authentication, better security as well as privacy, and almost transparent convenience.
I can't wait for it to launch this fall.
Read the full macOS Catalina Preview

Rene Ritchie is one of the most respected Apple analysts in the business, reaching a combined audience of over 40 million readers a month. His YouTube channel, Vector, has over 90 thousand subscribers and 14 million views and his podcasts, including Debug, have been downloaded over 20 million times. He also regularly co-hosts MacBreak Weekly for the TWiT network and co-hosted CES Live! and Talk Mobile. Based in Montreal, Rene is a former director of product marketing, web developer, and graphic designer. He's authored several books and appeared on numerous television and radio segments to discuss Apple and the technology industry. When not working, he likes to cook, grapple, and spend time with his friends and family.