iOS 7 Security: The good, the bad, and the controversy

An in-depth look at the security improvements, trade-offs, and ongoing challenges in Apple's latest mobile operating system, iOS 7
As with nearly all software updates from Apple, iOS 7 brought with it a large number of security updates for users. Ranging from entirely new features all the way down to minor tweaks and enhancements, there's a lot to discuss when it comes to iOS 7 security. iMore's editor-in-chief Rene Ritchie briefly touched on most of the changes in his iOS 7 review, but I thought it would be fun to take a closer look.
Activation Lock
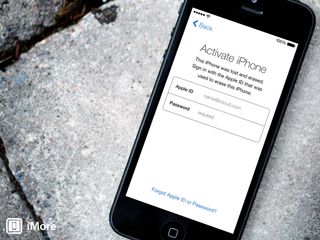
Activation Lock has been one of the most highly anticipated, talked about, and scrutinized security features of iOS 7. Activation Lock is a theft deterrent that works by leveraging Find My iPhone to help ensure if your device falls into the wrong hands, that another person won't be able to use it. When Find My iPhone is enabled on an iOS 7 device, Activation Lock is enabled by default, and it means your Apple ID and password will be required to turn off Find My iPhone, erase your device, and to reactive your device. This means if your iPhone gets stolen, a thief will have a much harder time trying to sell it.
Activation Lock will not prevent iPhone thefts, but it will make things more difficult on thieves.
Activation Lock has come under attack for a few different reasons. The first is many people have argued that this won't prevent theft. Common criminals who may not know about Activation Lock won't realize the disincentive to steal it. Some criminals may know about it, but steal it anyway to sell it to an unsuspecting buyer or scrap it for parts. And if you're arguing "Activation Lock won't prevent all thefts", these are valid supporting arguments. It's also true that locks and alarm systems on your home or car don't prevent burglaries or theft. However, they make you a much less appealing target. Activation Lock will not prevent iPhone thefts, but it will make things more difficult on thieves which should result in the number of overall iPhone thefts dropping as more users move to iOS 7. Nothing will ever make iPhones 100% theft-proof, but the goal is to set up hurdles that make the effort required for criminals not worth the potential monetary gain.
The second argument I've seen against Activation Lock is that we're going to see a rash of iPhone users forgetting their Apple ID & password, locking themselves out of their own devices, and being left with an expensive paperweight. This could happen to a user, but Activation Lock is designed in such a way as to make this as unlikely and difficult as possible. As mentioned above, your Apple ID and password are required to reset your device. In addition to the added security, this makes it more difficult for users to erase their device, only to realize later that they don't know their password to reactivate it. Also, when you reset your device and are prompted for your Apple ID and password, this is in order to disable Activation Lock. Part of the reset process for iOS 7 includes disabling Activation Lock. This has the added benefit of helping to ensure that if you're buying somebody's old iPhone that Activation Lock is disabled before you get it.
Of course, it's still possible that maybe something happens to your device and you're forced to put it into DFU mode and do a factory restore. In this case, you will not be able to activate your iPhone and set it back up until you enter your Apple ID and password. But even in this case, you have the ability to reset your password through the Apple ID portal, the same as you would have had to do prior to Activation Lock if you forgot your password. So let's say worst case scenario, you managed to reset your device with Activation Lock on, you've forgotten your password, and you can't answer your own security questions to reset it. It's no guarantee, but there's a decent chance at this point you could go into an Apple Store or store for your carrier, prove your identity to them, and have Apple perform an unlock from their end.
As you can see, it's fairly difficult to wind up with a brick of an iPhone. And it's probably a safe bet the the number of iPhone thefts prevented by Activation Lock will far outweigh the number of people who skillfully lock themselves out of their own phone. This makes Activation Lock a huge net win for iOS 7 users. Only time will tell, but I think we can expect to see, and hope that we do, a drop in overall iPhone thefts in the coming years as a result of Activation Lock.
iPhone 5s Touch ID

Touch ID is a new fingerprint identity sensor that resides in the Home button on the iPhone 5s. The sensor scans your fingerprint to unlock your iPhone, removing the need to enter your passcode every time you unlock your phone. In my experience, it's about as fast as doing a swipe-to-unlock without a passcode. With more than half of all smartphone users not using a passcode to protect their devices, the hope with Touch ID is to make securing your iPhone easier so more users will be likely to set a passcode.
Master your iPhone in minutes
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
Of course with the introduction of Touch ID came the question "how long until it's hacked?" and the answer turned out to be not long at all. The day after the release of the iPhone 5s came a video from the Chaos Computer Club demonstrating Touch ID being fooled by a fake fingerprint. The relevance of this has been a point of controversy. On one side people are arguing that this renders Touch ID useless. On the other side you have people saying this doesn't negate the benefits of Touch ID for most 5s owners. The answer lies somewhere in the middle. Whether Touch ID is useful to you will depend in your situation and what you hope to get out of Touch ID. Before we look at some Touch ID scenarios, let's cover a few specifics of how Touch ID works.
The primary use of Touch ID for most is to unlock an iPhone (though it can also be used for iTunes and App Store purchases). Rather than enter your passcode to unlock your phone like you normally would, you place a registered finger tip on the Home button, iOS checks the print, and if a matching print is found, the device is unlocked. There are a few caveats to this though. The first time you unlock your phone after a restart, your passcode must be used. If you want to change any lock screen settings on the phone, your passcode will also be required. If you have no unlocked your device in 48 hours, your passcode will be required. Finally, after 5 failed attempts with a fingerprint, your passcode will be required. With these rules in mind, let's look at some of the scenarios for Touch ID.
The benefits of Touch ID
The vast majority of iPhone users likely fall into two buckets: no passcode and simple passcode. For people who previously used no passcode at all, the convenience of Touch ID makes it much more likely that more people will set a passcode. As I said previously, using Touch ID is about as fast as using swipe-to-unlock on a device with no passcode set. Most users no longer have any good excuse for not setting a passcode if they have a 5s. Devices get lost and devices get stolen; it's a fact of life. Having a passcode on your device means not having to worry quite as much about some stranger poking around your device, looking at your personal photos, posting on Facebook, and generally meddling around in your stuff.
Touch ID makes it much more likely that more people will set a passcode
For users who were already using simple passcodes, consider using a more complex one. Instead of entering your passcode dozens, or even hundreds of times a day, it's now possible to go days without having to enter it at all. Consider using a numerical passcode more than 4 digits. If you use all numbers, iOS will present you with the quick-to-use number pad. If you're feeling particularly adventurous, try upgrading all the way to a complex, alphanumeric password. With Touch ID's convenience, you have a good opportunity to increase the security of your passcode.
Who should avoid Touch ID
As was mentioned, Touch ID can be fooled. The process isn't what you would call trivial, but it can definitely be reproduced, and has been. It's unlikely to be performed by a casual thief who grabs your phone or picks it up somewhere, but is perfectly suited for a targeted attack where an individual or group wants to acquire the contents of your phone. If you're worried about this sort of thing, then Touch ID may not be for you. Although it's also worth noting that in these situations, if you're entering your passcode dozens of times a day on your device, it's also feasible that somebody could monitor you until they are able to capture your passcode being entered.
Concern has also been raised about the fact that somebody such as a spouse or significant other could use your hand to unlock your phone while you're asleep. If you fall into the category of people worried about this, I guess don't use Touch ID, and maybe go to some couples counseling to address some issues.
The final scenario I want to specifically address is concerns over the Fifth Amendment. An opinion piece over on Wired.com raises the concern that a fingerprint may not be protected by the Fifth Amendment, while passcodes are. I encourage everyone to read the Wired article, but the gist is that while a password is something you know and can be considered testimonial, a fingerprint is not. A fingerprint is something you possess, like a key, which police could require you to turn over to them. Is this something most users need to worry about? Probably not. However, it's a very valid concern for anybody that may find themselves in such a predicament. If this is a concern for you, then Touch ID may not be a good idea. If this isn't a daily concern for you, but you find yourself in a situation dealing with law enforcement where it becomes a concern, consider powering your iPhone off. Remember that your passcode will need to be entered every time the phone is turned on.
To Touch ID or to not Touch ID
Touch ID is not one size fits all. As a user you will need to evaluate your situation and the possible risks to decide if Touch ID is a good idea for you. Personally, I keep a passcode on my device to protect my data in the event that my device is lost or stolen. I ask my wife to unlock my phone and check something all the time when I'm driving or have my hands full, so she knows my passcode anyway. I unlock my phone a lot and Touch ID is a welcome reprieve from entering my passcode every time. For me, the convenience far outweighs my concerns of being targeted for an attack. And if I were to fall victim to such an attack, my hope is that I would notice my device missing and be able to wipe my device via Find My iPhone before somebody was able to unlock it.
Weak Personal Hotspot passwords
Back in June, some researchers discovered that iOS had a rather weak and predictable method for generating Personal Hotspot passwords. In iOS 6 and earlier, the password was created by choosing a four to six character word from a dictionary only including 1,842 words, then appending a four-digit number. This resulted in default passwords like "poems6235". With a relatively low number of possibilities, researchers were able to brute force Personal Hotspot passwords in less than 50 seconds. iOS 7 users rejoice.
iOS 7 generates seemingly pseudo-random, 12-character, alphanumeric passwords. This is a huge improvement and makes brute forcing the password impractical. Though for any users who updated from iOS 6 to iOS 7, the password stays the same as it was in iOS 6. This is presumably to maintain compatibility with any devices previously configured to connect to the Personal Hotspot. If you updated from iOS 6 and have been using a default Personal Hotspot password, be sure to set your own password to avoid brute forcing by anybody attacking iOS 6 default passwords.
No more juicejacking
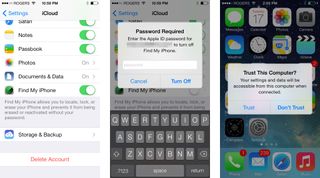
At Black Hat earlier this year, researchers presented their findings on a malicious charging station dubbed Mactans. The attack, also called juicejacking, had the ability to surreptitiously install malicious software onto your phone while also grabbing a copy of your data if you unknowingly plugged your phone into one of the malicious chargers. This relied on the fact that prior to iOS 7, iOS devices did not require user authorization before establishing a trusted connection between a device and a computer; the device only need be unlocked.
As of iOS 7, a user must explicitly trust a computer the first time it is connected before a trust is established. When a device is plugged in to a computer for the first time, a prompt appears asking the user to Trust or Not Trust the computer. Obviously if you're at the airport trying to charge your phone from a wall outlet and you're prompted to trust a computer, you should tap Not Trust. Even better, trust is not required to charge a device. This means even if you want to charge your device on a friend or co-workers computer, you don't have to allow it to transfer any data. With that said, it's still probably best to not just go around plugging your iPhone into random USB ports.
Lock screen bypass

As you've probably heard, several lock screen bypasses have been found in iOS 7, including the latest version, iOS 7.0.2. These bugs make it possible for an attacker to access certain information on your phone, even if it is locked. Depending on the bypass trick used, different information might be available, but generally speaking these bugs can grant unauthorized access to your photos & contacts, and allow a person to post to Twitter or Facebook as you (if you have Twitter and Facebook accounts configured in Settings).
These are definitely security bugs, there's no denying that. The good(?) news is such bugs existed in iOS 6. At the very least, you're no more at risk by updating to iOS 7. There also haven't been many reports of this actually being exploited in the wild. The bugs seems to provide more novelty for people than actual usefulness in stealing a user's address book. Apple fixed a lock screen bypass bug that had been found in 7.0 when they released 7.0.2. They will surely release another update that includes fixes for the bypass bugs that have been found since then.
If you're concerned about being affected by Passcode exploits, you can decrease the surface area of possible bugs by disabling Siri and Control Center on the lock screen.
iOS has to be able to access your contacts while the device is locked in order to show caller info. Photos presumably can't be blocked entirely because you can use the camera from the lock screen and iOS has to be able to save those photos to the device. Most of iOS' filesystem is encrypted and completely inaccessible without providing your passcode or fingerprint. These special cases like Photos and Contacts need to stay accessible for certain lock screen functionality, and limiting a user's interaction with those areas requires proper sandboxing by Apple. Given the history of these bugs, we'll probably see more of them pop up after the current batch is fixed and the cycle will continue.
If you're concerned about being affected by Passcode exploits, you can decrease the surface area of possible bugs by disabling Siri and Control Center on the lock screen. In the case of Twitter and Facebook, you can prevent abuse there by not signing in to those accounts in iOS Settings and instead using 3rd party apps. Hopefully at some point Apple figures out a way to properly sandbox these apps and end this cat and mouse game for good.
Siri security flaw

You've been able to use Siri from the lock screen by default since her introduction in iOS 6. It's not a security flaw. Stop saying it is. Go change the setting if you're so worried about it; that's why it's there.
Changes to user permissions
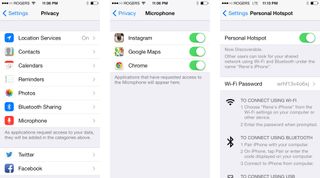
Back in February, iMore raised the issue that apps did not have to get a user's permission in order to access a device's microphone or camera. iOS 7 brought some changes to user permissions. First let's look at the good.
Microphone has been added under the Privacy section of Settings and apps must now get a user's permission before accessing the microphone. This is good news for user privacy as it means apps won't be able to record audio from your device without your knowledge. In addition to the microphone, Motion Activity is another new addition to Privacy, though it only shows up on the 5s. The 5s' new M7 motion coprocessor tracks and records movement information about your device on a much more granular level than previous iPhone models. The potential sensitivity to such information combined with the fact that many apps will have no business accessing this information means that it makes sense for apps to have to request permission. M7 data doesn't pose the greatest of privacy threats, but it's a wise move on Apple's part to restrict access to it.
Apps still don't have to request access to use the still camera.
Now let's look at the bad. Apps still don't have to request access to use the still camera. Any apps that wish to record video have to ask for permission to access the microphone, but even if permission is denied, they can still record video, it just won't have any sound. The threat of not requiring user permission is that any app can access the camera. Any app can take photos without a user's knowledge or consent. Any app can record video without your knowledge. That's a concern. A malicious developer could create an app that takes photos at a set interval, or records video, while the app is running, then uploads those photos or video to their server. Camera access is certainly something that not all apps need, so why not require that apps get permission to do it? There may be a good reason that Apple doesn't want to put the camera under the Privacy umbrella, but I don't know what it is.
The other item I would like to see added under Privacy is iBeacon. Some of you may already be screaming "they are under Privacy you moron!" but hear me out. iBeacons are new to iOS 7 and they are Bluetooth 4.0 Low Energy devices that can effectively act as micro-locators. They're already being adopted by Major League Baseball for placement in stadiums as a way to customize a user's experience with MLB's At the Ballpark app depending on where they are within a stadium. Instead of simply know that you're in the vicinity of the stadium, iBeacons through the ballpark can communicate with your phone to give it a much more granular idea of your location.
Technically speaking an app wanting to make use of iBeacons does have to get a user's permission first. The trouble is that permission is lumped in under Location Services. That's certainly a reasonable grouping to put iBeacons in, but the problem is iBeacons take location tracking to an entirely new level. Let's use the Target Store app as an example. The current app requests access to Location Services when you first run it. One of the purposes of this is to help me find a Target near me, which makes perfect sense. This is a permission that I would be inclined to grant for a use like that. Of course, I've now also given Target permission to use iBeacons as part of Location Services. This could conceivable be used to track my movements through the store. Perhaps Target will decide they want to see which sections a customer spends the most time in, and taylor the app's behavior to better accommodate that. They could display ads and products that they think would appeal to me based on which sections of the store I walked through. This usage also has its merits, but I want no part of it. And as a user, I should have the power to determine which apps can track me at such a fine level of granularity.
You can work around this by just disabling Bluetooth, but that's a hack and one that many average consumers may not even consider. The proper solution is to pull iBeacons out from the Location Services umbrella and assign them their own explicit permission. People have a right to know about the behavior of the apps that they use. Of course apps aren't a glass box that we can see all the inner-workings of, but privacy controls are one of the few mechanisms we have to exert some control over what the apps on our phones can and cannot do.
Overall, iOS 7 took a couple of steps forwards and a few steps back when it comes to user permissions. This is an area of iOS that seems to change with every major update. I hope that by the time iOS 8 rolls around, we'll have a few more additions to the Privacy section of Settings.
Block Contacts
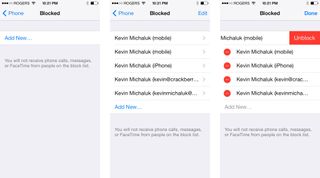
Let's end this on a high note. iOS 7 brings with it one of the most requested features from iPhone users (in my not-at-all official poll of friends who have asked how to do this over the years); the ability to block phone numbers. Searching Google for answers on how to do it yields millions of sites where users have been asking and trying to figure out how. Rejoice, friends. The day is finally here.
iOS 7 allows you to block phone calls, text messages, and iMessages from any contact. Telemarketer interrupting your... well... anything at all, since not even the most mundane and boring tasks on Earth make you wish a telemarketer would call. Just got a new number and the previous owners' bill collectors are harassing you? By tapping the info button for any recent caller in the phone app, there is now a button near the bottom for "Block this Caller". The same option can be found in Messages by tapping on a message, tapping Contact, then tapping the info button.
While the option says "Block this Caller", it actually applies to texts and iMessage as well.
While the option says "Block this Caller", it actually applies to texts and iMessage as well. If you block a caller, no calls or messages from that contact will come through on your iOS 7 device. In the case of iMessage, the sender will see "Delivered", but you'll never get the message (this could be problematic in some cases, but let's not look a gift horse in the mouth). If the person tries calling you, the call will go directly to voicemail and the voicemail will go into a "Blocked Messages" group that can be found at the bottom of your voicemail. Okay, so maybe we do need to look a gift horse in the mouth. This is wonderful for callers you truly never want to hear from; telemarketers, robocalls, crazy ex's, etc.
The downside is the way the blocked communications are handled could make it extremely difficult to figure out why you're not getting any messages from somebody if you accidentally block them. Your messages will get through to them, but any responses will disappear into the ether. Voicemails, while retrievable, will likely go unnoticed unless it occurs to you to check your Blocked Messages. The transparency of the block from the blocked contact's perspective seems ideal for a lot of scenarios. But for some situations it could be nice to make the block obvious to the contact. In fact, I would rather have spam callers get completely shut out than allow them to continue to leave voicemails. This would also make it much more apparent why you haven't heard from your old friend in a while if it turns out that you blocked them by mistake.
Nit picking aside, the ability to block contacts is a wonderful and welcome addition to iOS. It's been a long time coming and I'm thrilled to see users finally get the power to block the scummy texters and callers of the world.
Final thoughts
Overall I'm very happy with iOS 7, as a whole, but also specifically from a security and privacy standpoint. For the vast majority of users, iOS 7 offers some nice security and privacy enhancements over iOS 6. I'm eager to see the impact that Activation Lock has on thefts. I love Touch ID and can't imagine going back to a phone that doesn't have it. I get an almost worrisome amount of delight from blocking unwanted callers. There are definitely a few things I hope get added or changed in a future update, but I'm pleased with the direction Apple continues to head and look forward to what it brings in the future.